Remove the risk to your organization's revenue, data, and customers from bad open source packages
When you don’t have a continuous view of where end-of-lifed, abandoned, or insecure packages exist in your applications, your only defense is to scan for existing vulnerabilities and fix what you find.
Bad packages lead to more vulnerabilities—many of which are difficult to fix. This is slowing your application development team down, and creating additional invisible risk for your security team to manage.
Tidelift takes a unique, data driven approach to addressing the issue of bad packages. Tidelift partners with the maintainers of thousands of the most-relied-upon open source packages and pays them to implement industry-leading secure software development practices and document the practices they follow. The result is a unique source of cross-ecosystem package intelligence that customers use to identify and eliminate bad packages.
Tidelift’s package intelligence can be easily integrated into your preferred workflows using our flexible APIs or by adopting our web UI and CLI capabilities.
by eliminating attack entry points through bad packages
by reducing vulnerability fire drills from insecure or undermaintained packages
by building with healthy and resilient open source packages
by saving costly manual package evaluation time
When researching and evaluating open source packages to use, Tidelift’s package recommendations provide an excellent starting point. The recommendation is a holistic evaluation of the package, and whether it is developed and maintained in a way that would make it a good fit for application development.
It is also easy to undertake deeper package analysis with answers to questions such as:
Learn more about using our APIs to evaluate packages
Learn more about using our web UI and CLI to evaluate packages
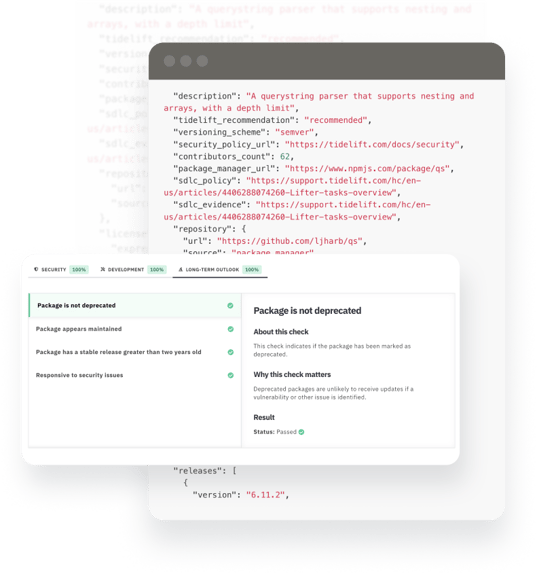
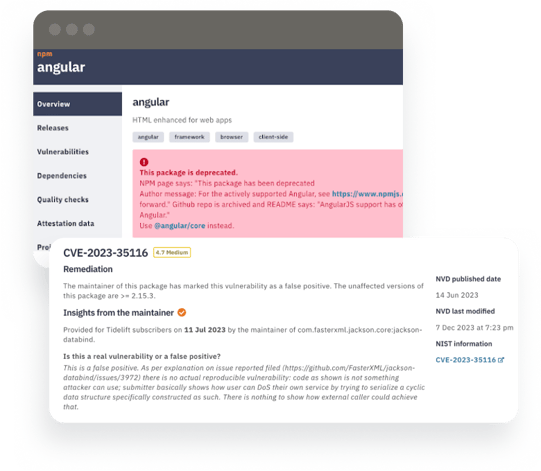
Open source packages are constantly changing and it is important to monitor and review updates after making the initial decision to use a package. Tidelift makes it possible to identify bad packages through early warning signs such as:
Learn more about using our APIs to monitor packages
Learn more about using our web UI and CLI to monitor packages
While it is ideal to identify and avoid bad packages in the first place, most organizations will have already adopted a significant number of packages without having done the upfront research.
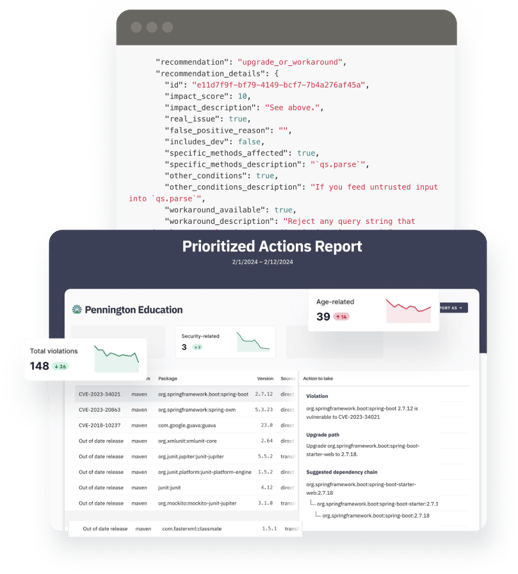
Tidelift helps organizations evaluate their existing open source dependencies and prioritize the work to migrate away from bad packages by answering questions such as:
Many maintainer partners also provide additional insights that can be used for prioritizing vulnerability remediation, including:
Learn more about using our APIs to eliminate bad packages
Learn more about using our web UI and CLI to eliminate bad packages

jackson-databind

minimist

urllib3

SockJS
Tidelift customers play a direct role in ensuring the packages they rely on keep getting better because package maintainers are paid based on factors that include customer usage. Maintainers use this income to improve the secure development practices they have in place, to document these practices, and to commit to maintaining them over time.
This means that customers can use open source with confidence, knowing that experienced maintainers have made the commitment to ensure the package follows enterprise level secure software development practices, and have the income they need to ensure it stays resilient and healthy into the future.
Learn more about how you can identify at-risk projects within your organization
.png)
One question we get a lot when talking to customers: how does Tidelift go hand in hand with software composition analysis tools, like Black Duck or Snyk or Mend.io? Short answer: Tidelift is proactive, SCA is reactive.

When news of the critical vulnerability in popular Java logging tool Log4j broke, the team at EMPLOYERS® was ready.
.png)
Check out the new state of the open source maintainer report which included 11 key headlines coming out of our new survey of over 300 open source maintainers.